Legacy Application Migration: How to Move to the Cloud?



Legacy application migration has become a buzzword that often finds its way into IT discussions. But what does it really mean, and why should you care?
Legacy application migration is the process of upgrading or using legacy programs and transitioning aging or outdated software systems to modern platforms. Why does it matter to migrate legacy anything? Because legacy applications, while once the crown jewels of tech innovation, can become ticking time bombs. They pose security risks, hinder agility, and are often costlier to maintain than to replace.

The pot of gold at the end of the migration rainbow includes more cloud computing resources, enhanced performance, improved security, cost savings and the ability to embrace new technologies, business processes, and methodologies. It’s like trading in your old flip phone for a shiny new smartphone – a game-changer.
Content
Old software applications, known as legacy applications, sometimes reach a point where they’re no longer up to the task. In this part of our guide on legacy application migration, we’re going to explore the signs that tell you it’s time for an upgrade. These signs are like warning lights, indicating that your old software needs a refresh.
From the software company no longer providing support to your application crashing too often, these signals are like clues that it’s time for migrating legacy applications.
One of the earliest signs that may trigger the need for migration is dwindling vendor support or outdated software systems. When the software or platform your application relies on is no longer receiving updates, patches, or security fixes, it becomes increasingly vulnerable.
Performance degradation is like the warning lights on your dashboard flickering. Sluggish response times, longer loading periods, or increased resource utilization are indicators that your legacy application may be struggling to keep up with modern demands.
Just as a car breaking down frequently signals mechanical issues, frequent application crashes are a glaring sign of underlying problems. These crashes disrupt productivity, frustrate users, and can even result in data loss or corruption.
Users are often the first to experience issues, and their feedback can be invaluable in identifying pain points within the application.
In summary, recognizing the signs that herald the need for migration, conducting evaluation of the existing system, and assessing the potential business impact are foundational steps in the decision-making process. Organizations must proactively address the health and well-being of their IT systems to ensure resilience, security, and continued competitiveness in the digital landscape.
In IT, it involves defining goals, assessing scope, and creating a detailed plan with a well-defined timeline.

Let’s delve into these crucial aspects with a professional IT perspective:
Objective Clarity: When initiating a migration, it’s paramount to define your business applications goals with absolute clarity. Ask yourself, “What are we trying to achieve with this migration?” Is it enhanced system performance, increased scalability, cost reduction, continuous integration or perhaps modernization to meet evolving business needs? By articulating these objectives precisely, you establish a clear direction for the system migration project.
The Road ahead: Similar to planning a road trip, understanding the scope of your sstem migration efforts is crucial. It involves comprehending the full landscape of the migration effort. Scope assessment includes:
Complexity: Evaluate the intricacy of network architecture in your existing IT environment. Are there numerous dependencies, legacy systems, or third-party integrations? Recognizing complexity is vital to anticipate challenges.
Scale: Determine the scale of migration. Is it a single application, a suite of systems, migrating legacy systems and applications, or an entire data center? Understanding the breadth of migration helps allocate resources effectively.
Dependencies: Identify dependencies between applications and data, as well as any interdependencies within the migration project. Mapping these dependencies is akin to plotting waypoints on your journey to avoid unforeseen “potholes.”
Precise navigation: A migration plan is your roadmap for the journey. It’s more than just a list of tasks; it’s a strategic document that guides every phase of migration. Elements of a well-structured and complete migration plan include:
Timelines: Define specific timelines for each new system and migration phase. Establishing deadlines for milestones keeps the project on track and ensures alignment with business objectives.
Milestones: Milestones are like signposts along the way. They mark significant achievements and progress during migrating legacy software. Achieving milestones provides a sense of accomplishment and helps track project success.
Contingency strategy: Like having a backup navigation system, a contingency strategy is essential. It outlines actions to take if unexpected challenges arise. Contingencies could involve rollbacks, alternative routes, or resource reallocation.
Resource allocation: Allocate resources, including personnel, equipment, and budget, in a well-considered manner. This ensures that the project has the necessary support throughout its lifecycle.
Risk assessment: Consider potential risks and challenges at each phase of the migration. Develop mitigation strategies and incorporate them into the plan of moving your applications to the cloud.
In conclusion, the planning phase of migration is the foundational pillar upon which the entire project stands. Preparation minimizes uncertainties, reduces risks, and sets the stage for a successful migration journey in the dynamic landscape of IT.
Migration strategies are like different routes on a map: rehost, replatform, or refactor. Each has its pros and cons, and the choice depends on your business requirements.
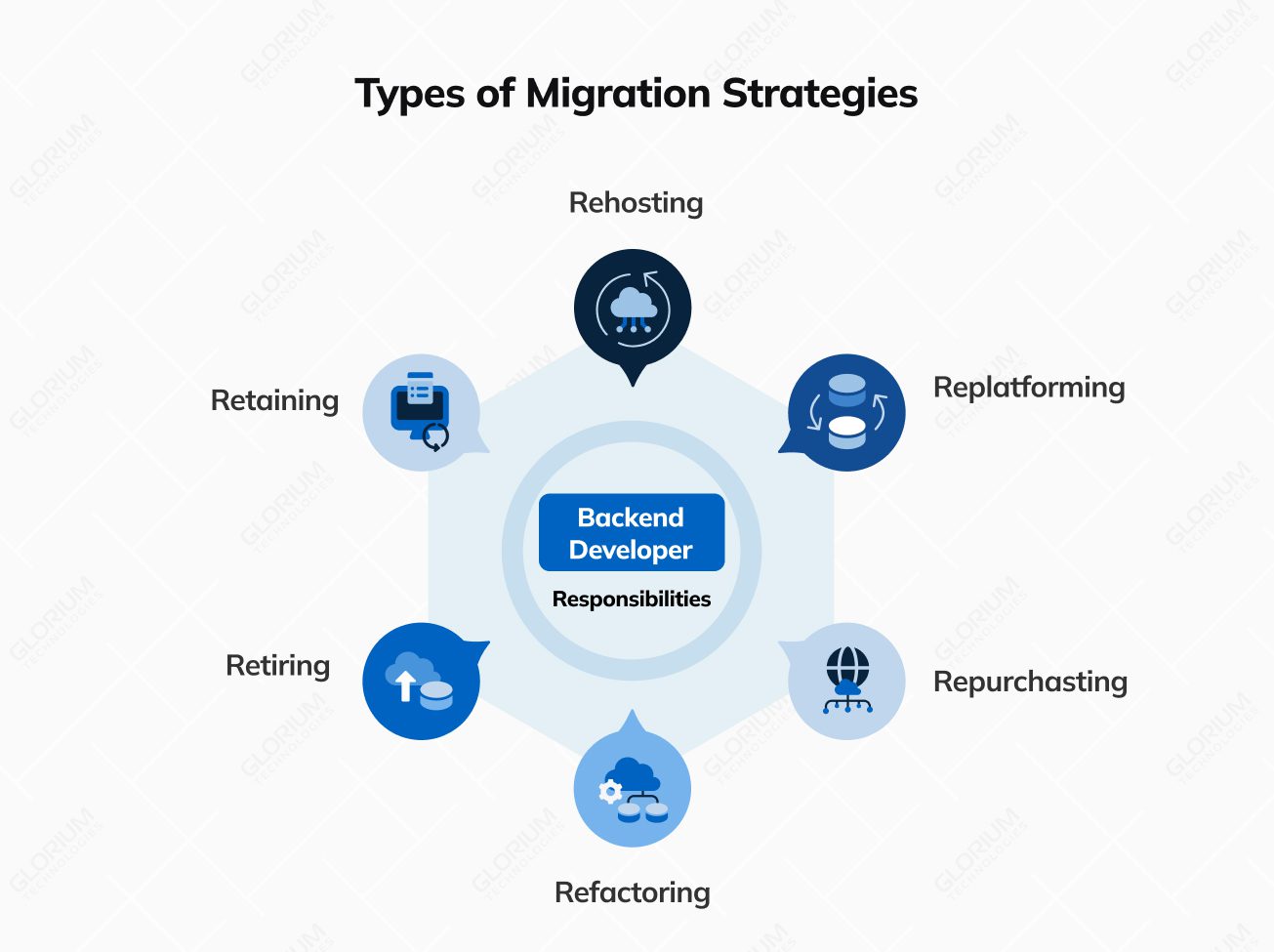
Description: Rehosting entails relocating the existing application to a new environment with minimal alterations. This process typically involves transferring the application and its data to a different hosting infrastructure, often within a cloud computing environment. The primary objective is to reduce costs while maintaining the core functionality.
Pros: Rehosting is an economically efficient and relatively swift option that minimizes disruption to ongoing operations.
Cons: While cost-effective, this strategy may not bring significant improvements in terms of functionality, scalability, or performance. It might not address underlying issues present in the legacy code.
Description: Replatforming represents a step beyond rehosting by making selective adjustments to the application to ensure compatibility with the new environment. These adjustments could involve updating elements like the operating system, middleware, or database while preserving the core code.
Pros: Replatforming enhances compatibility and offers the potential for improved performance and scalability. It typically carries a reduced risk compared to a full-scale rewrite.
Cons: This strategy may not fully capitalize on modern technologies, and certain legacy issues may persist.
Description: Refactoring is a more comprehensive approach involving the rewriting or rebuilding of specific sections of the legacy application’s code using contemporary development practices and technologies. This strategy seeks to enhance code quality, maintainability, and scalability while preserving the application’s core functionality.
Pros: Refactoring yields improved performance, scalability, and maintainability. It also presents an opportunity to introduce new features and align the application with current business needs.
Cons: While offering substantial benefits, refactoring tends to be more resource-intensive and time-consuming compared to rehosting or replatforming. The increased complexity may lead to longer project timelines.
Description: Rearchitecting involves a fundamental redesign of the application’s architecture to bring it in line with modern standards. This often necessitates the transformation of a monolithic application into microservices or adopting a new architectural pattern.
Pros: Rearchitecting offers advantages such as greater scalability, agility, and flexibility. It empowers organizations to leverage cloud-native technologies and embrace microservices architecture.
Cons: This strategy can be complex and resource-intensive, demanding a deep understanding and seamless integration of both legacy and modern technologies.
Description: In certain scenarios, it may prove more cost-effective to retire or sunset a legacy application, particularly if it no longer serves a purpose or if its functionality can be adequately replaced by off-the-shelf solutions or newer systems.
Pros: Retirement simplifies the IT landscape, reducing ongoing maintenance costs, and eliminating security risks associated with the legacy application.
Cons: Successful retirement may require meticulous data migration and careful planning to ensure a smooth transition for users.
Choose the strategy that aligns with your goals and resources.
When undertaking the complex task of migrating a legacy application to a third cloud platform, meticulous risk management is imperative to ensure a smooth transition. Here, we delve into the critical aspects of risk identification, mitigation strategies, and the paramount importance of data security, all articulated in a professional IT tone:
The first step in effective risk management is the identification of potential roadblocks and pitfalls that may disrupt the legacy system migration process.
Risks in the context of legacy application system migration, can manifest in various forms, including:
Data loss: During the migration process between legacy systems, there is a risk of data loss or corruption. This can occur due to data transfer errors, incompatibility issues, or mishandling of data.
Integration challenges: Legacy applications often have intricate dependencies and integrations with other systems. These integrations can pose challenges during migration to cloud environment, leading to compatibility issues or data synchronization problems.
Technical hurdles: The migration process may encounter unforeseen technical challenges, such as software conflicts, hardware limitations, cloud services misreadings or performance bottlenecks.
Resource constraints: Budgetary constraints, lack of skilled personnel, or inadequate existing infrastructure can hinder the legacy migration.
Once risks are identified, the next critical phase is to develop comprehensive strategies to mitigate these risks effectively. Here are key strategies:
Data backup: Rigorous data backup procedures should be in place before legacy migration commences. This ensures that a pristine copy of the data is readily available in case of data loss or corruption during the legacy applications migration process.
Thorough testing: Testing is the linchpin of risk mitigation. Rigorously test every aspect of the legacy migration process in a controlled environment before implementing it in the production environment. This includes both functional and non-functional testing to identify and rectify issues.
Contingency planning: Develop well-structured contingency plans that outline actions to be taken in the event of unexpected issues or failures. Contingency plans act as a roadmap for responding swiftly to challenges, minimizing downtime, and preventing data loss.
Data security during legacy applications cloud migration, is akin to transporting valuables in a secure armored convoy. The integrity and confidentiality of data must be upheld at all costs. Here’s how:
Encryption: Implement robust encryption mechanisms to protect data during migrating legacy aplications. This ensures that even if intercepted, the data from migrate legacy applications and systems remains unreadable to unauthorized parties.
Access controls: Enforce strict access controls to limit access to data during data migration, to authorized personnel only. This prevents unauthorized alterations or breaches while you migrate legacy applications.
Monitoring: Continuous monitoring of data flows and security protocols is essential. Real-time monitoring systems can detect anomalies and suspicious activities, triggering immediate responses.
In conclusion, managing risks and challenges in legacy application migration is a multifaceted endeavor. It begins with the identification of potential pitfalls, followed by the development of comprehensive risk mitigation strategies.
The migration phase is a pivotal juncture in the legacy application migration process to cloud environment, demanding meticulous planning and execution.
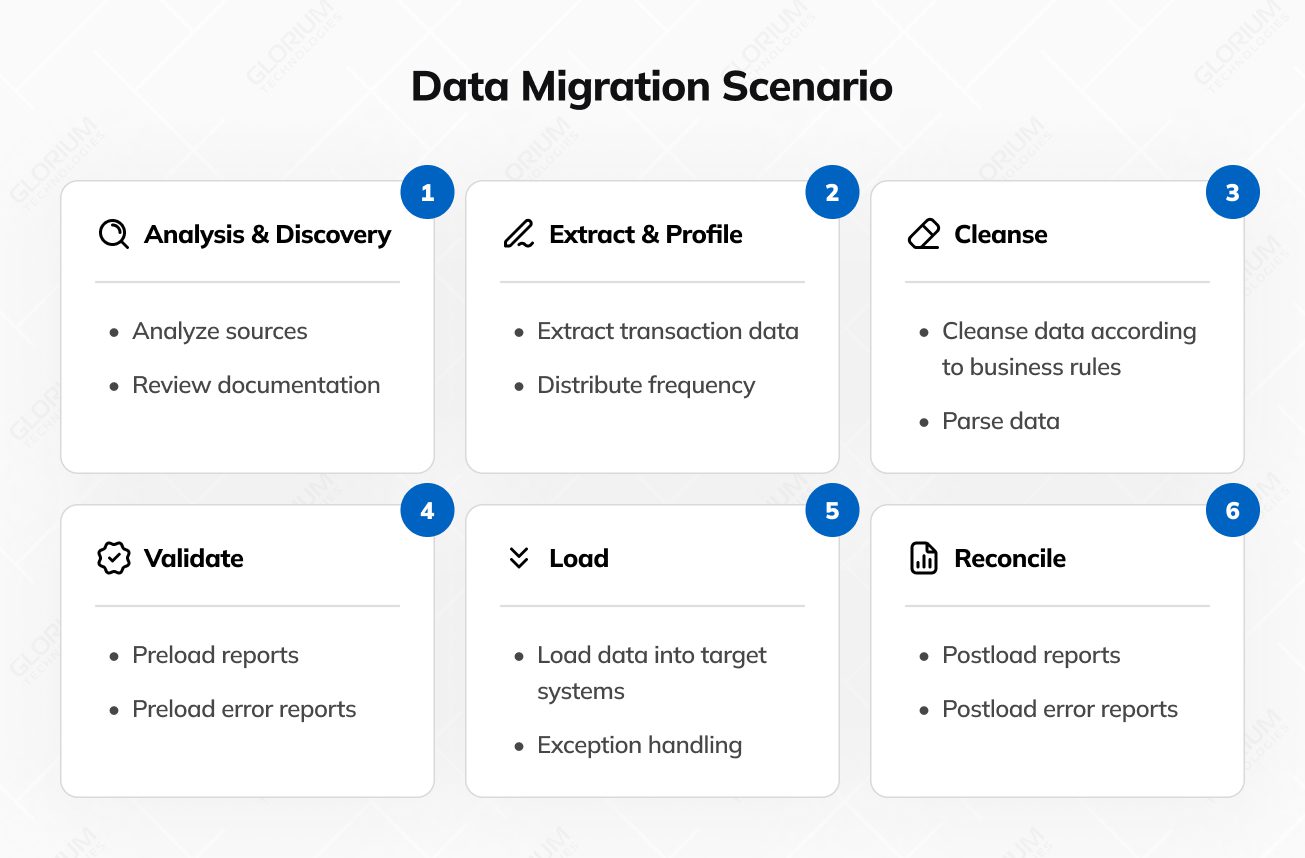
Here’s a closer look at this critical stage:
Data, often the lifeblood of an application, must be treated with precision and care. Data cleanup involves identifying and rectifying inconsistencies, redundancies, and inaccuracies within the already existing systems and data repositories. This cleansing process ensures that only relevant and accurate data is migrated, minimizing disruptions in the new, cloud infrastructure environment.
Compatibility is paramount during migrating legacy and applications to the cloud first. It entails assessing whether the existing and migrating legacy apps and software components, including software libraries, databases, and integrations, are compatible with the cloud migration target environment. Compatibility checks help identify potential roadblocks and the need for adjustments or upgrades to address during migrating legacy applications.
The private cloud migration plan, meticulously crafted during the planning phase, serves as the blueprint for the actual migration process. Following the cloud migration plan diligently is of paramount importance. It delineates the sequence of actions, timelines, and milestones. Deviations from the system migration plan should be well-documented and justified.
Constant vigilance is essential during legacy systems migration. Regularly monitor the progress of each migration task, cross-referencing it with the predefined timeline. Monitoring provides early detection of any deviations or complications, enabling timely intervention and corrective actions.
As a seasoned Project Manager with extensive experience in IT infrastructure and application migrations, I have overseen numerous legacy application transitions to cloud environments. Based on my experience, here are some key insights and recommendations for successfully managing such a migration:
In essence, migrating a legacy application is a highly structured and technically intricate undertaking that demands meticulous attention to detail. By embracing data cleanup, compatibility checks, and dependency management, organizations can ensure a seamless transition of legacy apps to a modernized environment.
Legacy application migration is not just about modernizing your IT systems; it’s about future-proofing your whole business operations. Embrace the change, choose the right legacy applications migration options and path, and navigate the IT highway toward a brighter, more agile, and secure digital future.
Legacy application migration is the process of transferring an older, outdated software system (legacy application) to a modern and up-to-date technology stack or platform. This is done to improve performance, security, scalability, and maintainability.
Legacy applications can become inefficient, insecure, and difficult to maintain over time. Migration is necessary to ensure that the software remains relevant, secure, and can meet evolving business requirements.
The duration varies significantly based on factors like the complexity of the application, chosen migration strategy, resources, and testing requirements. It can take several months to a few years.